Password Cleanse
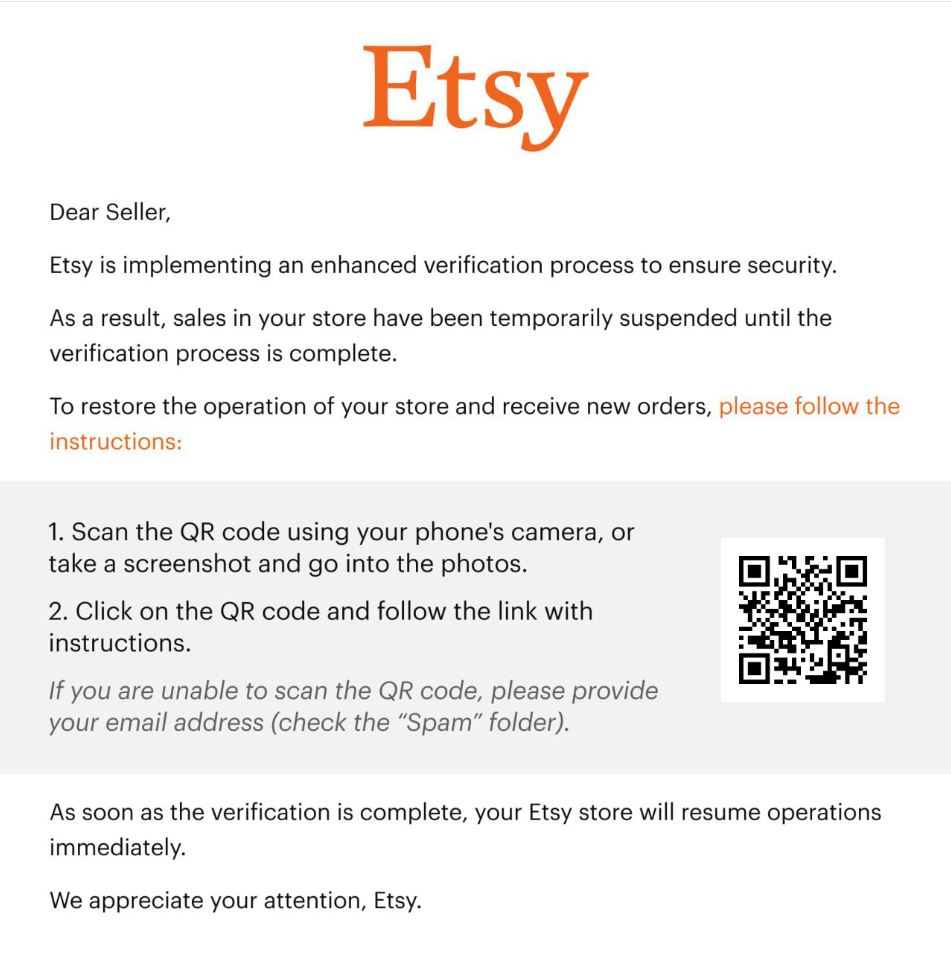
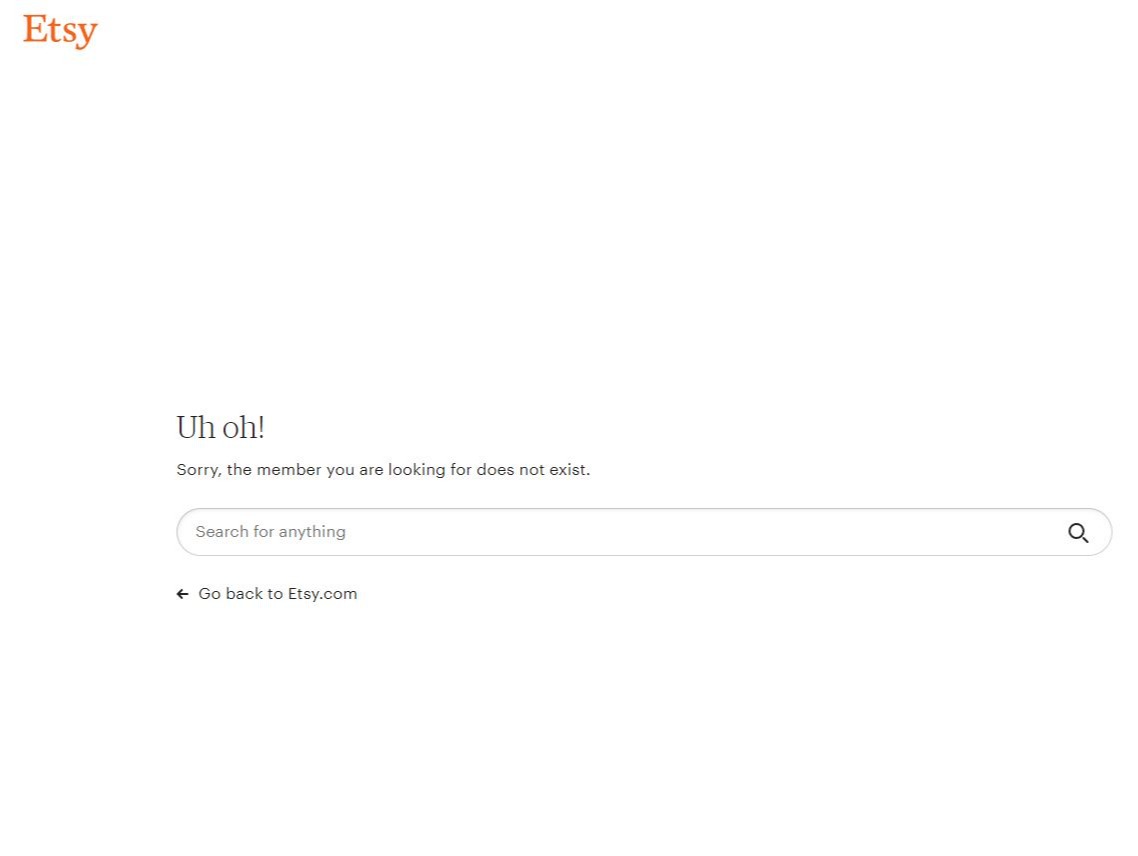
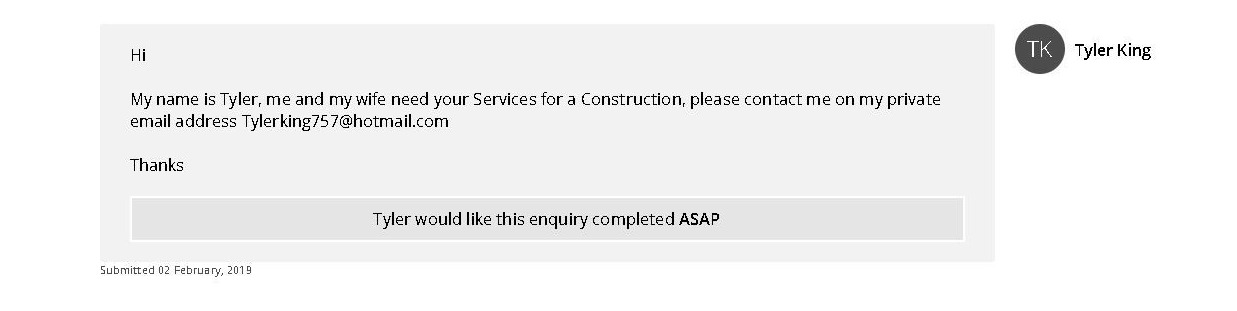
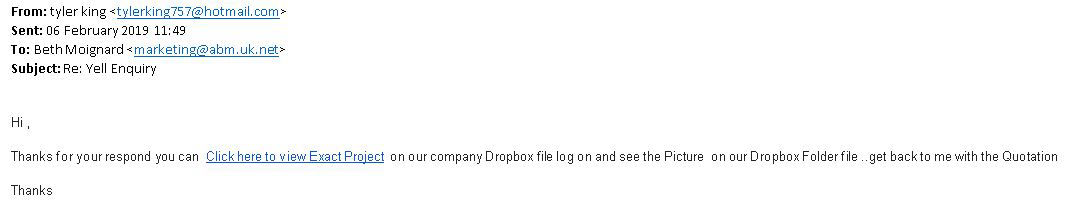
Let’s be honest — most of us reuse the same two or three passwords everywhere, add a “1!” at the end when we’re forced to change them, or stick with something we came up with years ago. It’s completely normal… but also exactly what cyber attackers count on. Over time, these habits create little cracks in your security without you even realising it. Old passwords get leaked, reused ones become predictable, and simple ones can be guessed in seconds with modern tools. That’s why taking a few minutes to do a password cleanse is one of the easiest and most effective ways to protect your business accounts. To help make that process quick and stress‑free, we’ve put together a simple step‑by‑step guide you can follow — and share with your team.
Identify the accounts you actually use: Start by pulling together a list of all the accounts you log into. Password managers already store the majority of your logins — use them as your starting point. Your phone likely shows you apps and services you’ve signed into, which can quickly remind you of what you access daily. Email inbox search can reveal login notifications or account creation emails that jog your memory.
Start updating your account passwords: Use strong, unique passwords ideally 12 characters long, a mix of letters, numbers, symbols, not based on personal information and no repeats! This step can feel daunting, so concentrate on higher value data first, things like banking, companies that have payment details, and highly personal information. (look out for our guide on how to come up with these types of passwords)
Turn on Multi - Factor Authentication: Again concentrate on high value accounts and if the option is there, always use MFA. We know it is a pain, but it has prevented so many breach opportunities.
Remove old and unused accounts: We all have those one‑off accounts — a free trial we signed up for, an app we tried once, or a login created on a whim and forgotten about. Even though you’re not using them anymore, your data often still sits there… along with any weak or outdated passwords you once used. These forgotten accounts can quietly reveal a lot about your password habits and make it easier for cyber attackers if the service is ever breached. Take a few minutes to go through your password manager, email inbox, or phone apps and close down anything you no longer need. Clearing out old accounts reduces risk, tidies up your digital footprint, and puts you back in control of your information.
Update your password manager(s): Save the newly updated passwords, remove duplicate entries.