
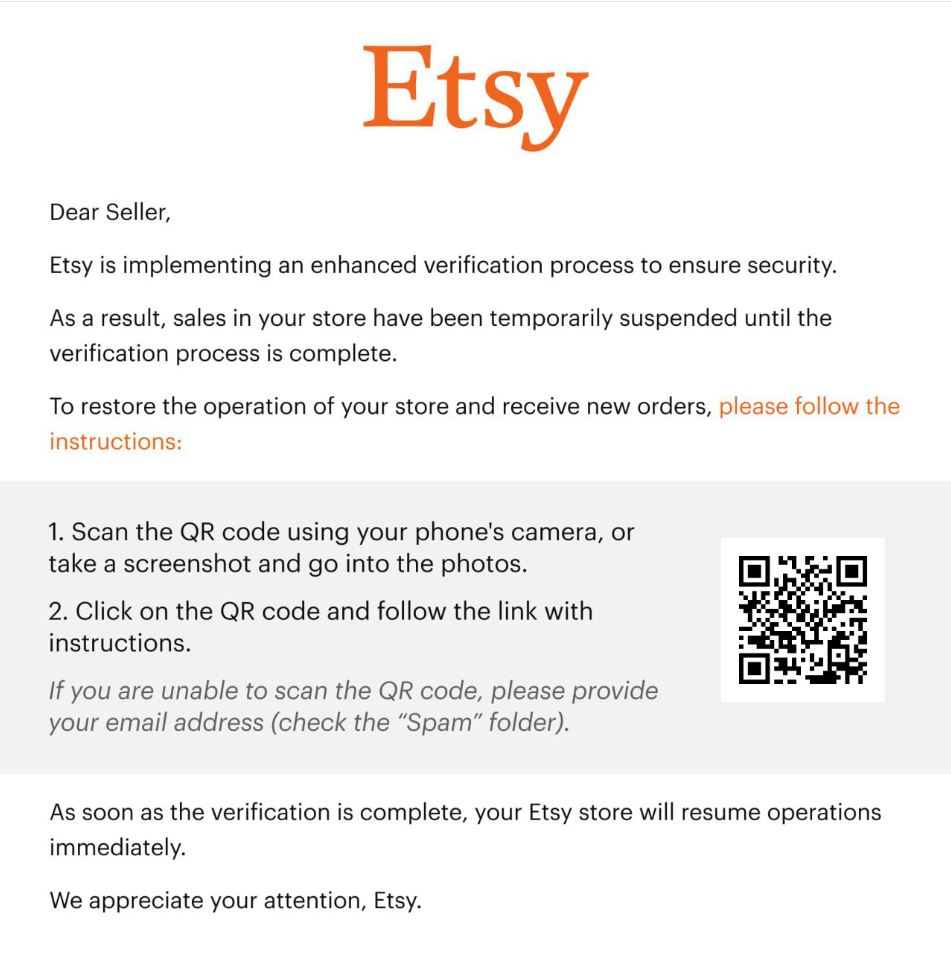
Balancing Innovation & Security
Click the button below to view our infographic on this topic. Be sure to use it how you wish and share the information with others.
Chichester | Hampshire | Sussex

Click the button below to view our infographic on this topic. Be sure to use it how you wish and share the information with others.
Underestimating the threat landscape:
SMEs often assume that they're too small to attract the attention of cybercriminals. However, hackers frequently target smaller businesses precisely because they may lack robust security measures.
Tip: You might not be able / might not require an all singing and dancing IT security setup, but every SME should have the basics, check out our content on this in our 'Business IT Security Basics Checklist'.
Neglecting employee training:
Employees can be both a business's greatest asset and its greatest vulnerability. Many SMEs neglect comprehensive cybersecurity training for their staff, leaving them unaware of potential risks like phishing attacks or ransomware.
Tip: Conduct regular cybersecurity training sessions for all employees. Include real-life examples and practical tips on identifying potential threats.
Inadequate password policies:
Weak or reused passwords remain a significant security risk. Many SMEs still do not enforce strong password policies, making it easier for cybercriminals to gain unauthorised access to critical systems.
Tip: Require the use of Multiple Factor Authentication (MFA) to add an additional layer of security, even if passwords are compromised.
Failure to regularly update systems:
Outdated software and systems are prime targets for cyberattacks. SMEs often postpone system updates due to concerns about disruptions, leaving their digital infrastructure vulnerable to exploitation. Businesses should also pay close attention to End Of Life (EOL) dates as this is an indicator of when security patches are ending for products you are using.
Tip: Develop a schedule for regular updates during non-operational hours to minimise disruptions. Prioritise critical updates.
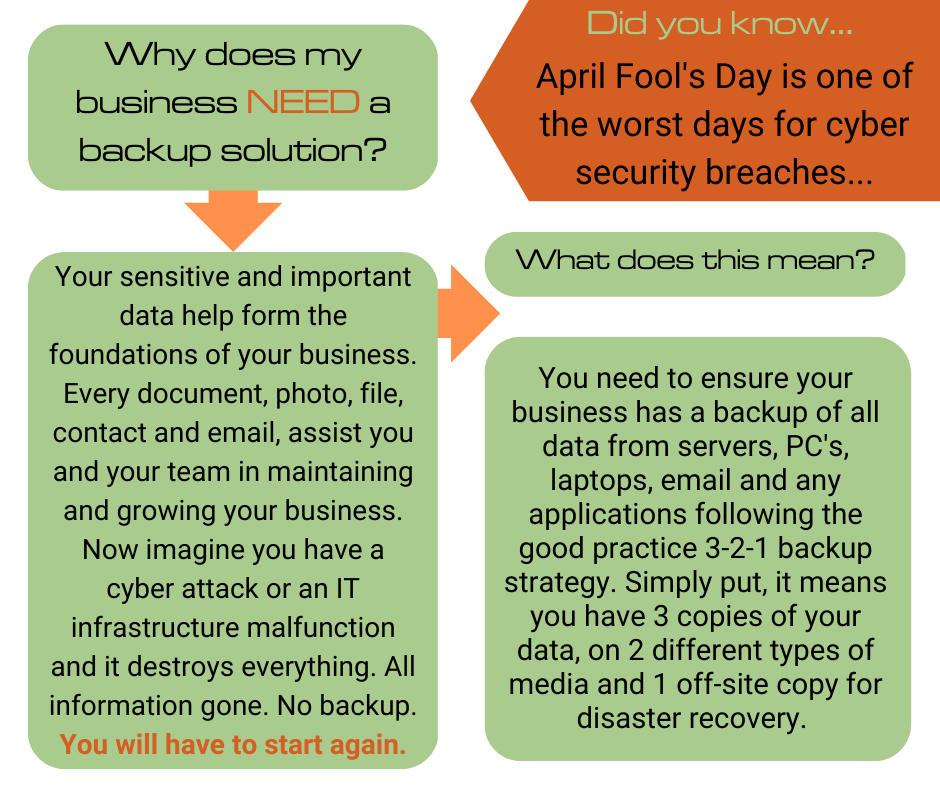
Lack of data backup and recovery plans:
Data loss can be catastrophic for any business. SMEs frequently underestimate the importance of robust data backup and recovery plans, leaving them vulnerable to ransomware attacks and therefore unexpected data loss.
Tip: Implement automated and regular data backups. Test the backup and recovery process to ensure its effectiveness in case of a cyber incident.
In the ever-evolving digital landscape, cybersecurity is not a luxury but a necessity for small and medium-sized enterprises. Recognising these common mistakes is the first step toward building a resilient cybersecurity outlook. Remember, cybersecurity is an ongoing process that requires constant attention and adaptation. By staying proactive and informed, SMEs can safeguard their digital assets and thrive in the digital age.

Click the button below to view our infographic! Be sure to use it how you wish and share the information with others.
Limit the damage caused by a hack
If you have had a huge security breach then these rules wont apply to you. We have more information on our IT security blog page, and we will create an email for you over the coming weeks to advise you on actions for a larger data breach. However, if you have been personally hacked, for example, you clicked a link on social media because your friend sent you a 'video you were in', or you downloaded a font on the internet from a questionable source, or you logged in to your account via an email, and it wasn't an official email, then these steps may help prevent further breaches.
Heighten your email spam filters
Be even more vigilant with your emails
Change all passwords, for all accounts that hold personal data
Encrypt your sensitive data and backup (be sure to have a clean backup)
If through social media, communicate the fact that you have been hacked
Install an effective anti-malware solution and run scans on your machine daily
Have an expert check over all of your technology and clean up any infections
Technology is slower than usual
Storage is full or very close to limits
Systems freeze and become unresponsive
Your technology is automatically shutting down or restarting
Noisy technology (like the sound of fans) or is it hot to touch?
Has the installation of anti-virus worked, or are you not able to install?
If your internet usage is high, the virus might be sending data back and forth
Navigating through files, you might see some unusual file types / encrypted files
Report the issue
Gain an expert opinion
Have a professional clean completed
Communicate with others that you have been compromised
Shut down the technology and do not touch it until an expert can help
Actions you can take to help prevent zero-click breaches
Practice caution always
Encrypt your sensitive data
Always research software you want to install
Be vigilant about where you give permissions
If something seems out of the ordinary, report it
Keep your device and software updated to latest update version
Celebrated to remind everyone about the importance of protecting data and keeping your systems secure. We have created content on the importance of backing up your data and some advice on creating a good-practice solution. We also suggest viewing our cyber security content on this page, have you followed the 'IT security basics checklist' above?
Don't panic. It happens to the best of us, these criminals have become highly capable at achieving their goals. We recommend following these steps:
(You can always contact us and we can deal with it)
If you have logged in to an account via the link, change the password, log out of all devices.
Warn your colleagues, run a virus scan, check SPF setup, does it warn you about non-genuine emails?
Be careful, it may have come from a correct email address who may have been hacked, check for spoofed email addresses.
(You can always contact us and we can deal with it)
If you have logged in to an account via the link, change the password, log out of all devices.
Warn your colleagues, run a virus scan, clear cache and history in your browser.
We recently learned of a case where a person wasn't able to send or receive emails in Office 365. Upon investigation it turned out that their account had been hacked, likely through clicking into a phishing email and then entering email address and password on a fake webpage. There is no indication that the password entered was even for the Office 365 account, however, because all of this persons passwords were similar with minor changes, it was easy to guess.
Your email is a gold mine because it allows cyber criminals access to your other accounts, AND to your contacts. For a personal account, this is unfortunate. For a business account, this is very serious.
It turns out in this case what had happened is the cyber criminal had set a rule for incoming emails, so all received would be automatically deleted. The reason why they did this was so they could mass send spam emails through the account; and without receiving any bounce backs or spam warnings from Microsoft, the owner wouldn't suspect any issues until too late. Luckily, Microsoft recognised the spam being sent and had blocked the account.
(The best solution in this case is to login, change the password, force logout of all devices and let Microsoft know about the problem.) This is a popular scam at the moment so please be mindful. The worst part is that lots of security solutions would not pick up on this. You will have to rely on strong passwords, being extra mindful about the emails you click on, and our main advice: Two-factor authentication to a mobile number not the email account!
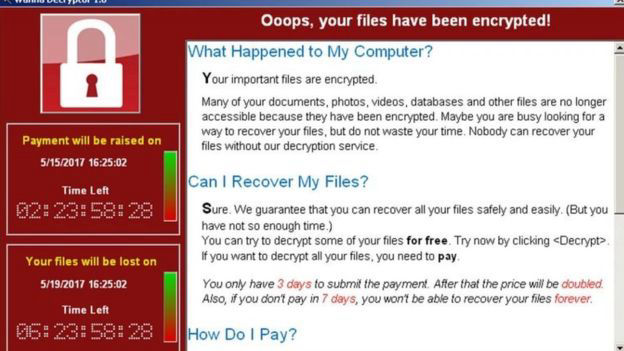
No matter how careful you are, getting a virus on your machine can sometimes happen. Different infections complete different tasks. Malware : This is a general term for a virus. This is an important word to know as some people may not refer to it as a virus or infection. The over all task of any malware is to gain unauthorised access to your machine via downloading malicious software.
It's aim is to block the user from gaining access to their files. It completes this by encrypting your data. (Essentially it changes the data into a code you have no idea how to unlock.) The only way to get your files back is to pay a ransom. However, it is more likely that you have lost them forever. This is why taking a backup of your files in a separate location is so important.
One of the most favoured malware among hackers. This is because they can target a whole company (or certainly a large number of people in a company), purely with the infection of one machine. Once the worm is implanted in your machine, it replicates itself and uses the network to spread further. It's aim can change depending on how it is coded. Either it will modify and delete files, or it will inject additional malicious software onto your system.

This is a very popular reference in film. Once installed its aim is to record all of the keystrokes you make. It records and sends this data straight to the hacker.
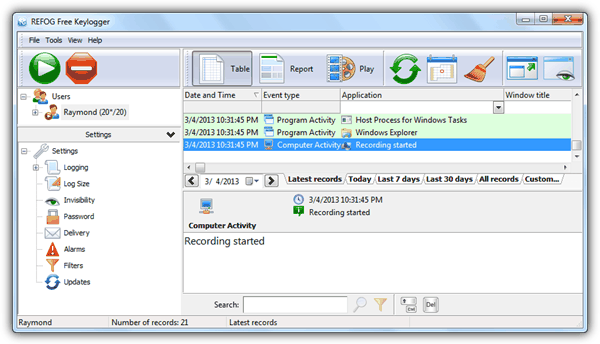
Much like the tale, the Trojan Horse disguises itself as a safe program to breach your systems. It may be a software you really like the sound of, and it might seem extremely popular. However, when installed it reveals it's true self and causes mayhem. Either deleting data, blocking data or spying on your sensitive information.
Also very popular in film. (Die Hard 4) It is installed to cause pop ups on your screen. Potentially in a flurry of random nasty websites and image ads. Or random pop ups that appear all over your screen and are therefore hard to avoid.
As it's name suggests this malware is used to view information. Relaying your important data to another person for them to use how they wish. (Usually for purchasing items online.)
Public WIFI has become a common selling point for many businesses. It is so easy to visit your favourite coffee shop and almost instantly have access to the internet, for free. But what are the dangers of using this open network? There are many precautions you can take to prevent a data breach.
Password Protection / Encryption - Businesses are helpful in providing a network that everyone can easily access. However, if this connection isn't secured through a password, or some level of encryption, it basically allows anyone to access at any time. Most people will use it to complete general tasks, but there is always that 1% that has bad intentions. Using it to read other people's data (MitM attacks), deposit malware or record data for further scams.
Man In The Middle - Or MitM attacks, are when someone uses a relay point between your connection and device to read your data. Your private work is no longer for your eyes only.
Hackers can use vulnerabilities in an infrastructure to deposit malware. Once on your device, it may have several different tasks to complete. The tasks they complete all lead to some kind of personal data being stolen and used maliciously. Fake Hotspots - (Or rogue access points) Trick you into thinking they are a legitimate connection. They potentially have a similar name, such as 'Peter's Cafe' could be 'peterscafe'. But unfortunately, you have connected to a hacker's hotspot and they can now view everything you look up. If they have set this up, it is likely they also have a software that can view the webpages you are looking at, and anything you may have entered into the web page, including your login details (If not encrypted).
Sensitive Data - If you desperately have to access your banking or other sensitive data, only use https sites. Do not use an application. If you can wait until you get home, or to an encrypted network, then do so.
Wi-Fi Settings / File Sharing - Do not leave your Wi-Fi and Bluetooth on if you are not using them, and turn off the auto connect option! This 'auto connect' function allows your device to automatically connect to any known networks in the area. As well as this, turn off your file sharing setting. This makes it harder for hackers to drop malicious files and malware onto your device.
Password - If you can, only connect to networks with passwords and a high encryption set up. The best places are the ones where you have to actively ask for the password.
Log Out - A simple mistake is leaving your account open, or just exiting the web page. Please log out of all accounts after you have finished using them.
Many of us like to use generic or simple passwords so we don't forget what they are, or for ease of use. However, this can be a dangerous comfort, especially in a business environment. 'Password1' has been the most common password used since security was a requirement. If this is used by you for any device - uh oh, maybe consider changing it? How do you create an effective password? What are the do's and don'ts of password use?
Password Creator - Sometimes it is hard to decide on a password. Everything seems guessable. There are several online generators that are great for extremely random codes. If not, we can suggest some passwords for you.
Try and make them based on hard to know information. For example, it will be hard for someone to find out your favourite childhood car, or where you met your partner.
I know it is tempting to keep them short and sweet. But a longer password is less likely to be guessed. For example, 'MiniCooperLoves1.6' has 18 characters! This is verified as a strong passcode (as it is above 16 characters) and would be hard for someone to guess. Capital letters, full stops, exclamation marks, symbols, slashes, underscores and dashes are great ways to make up the characters in your password, and in addition, make it more complicated. Lots of websites don't allow passwords without special characters now; and so it is a good idea to figure out a few passwords you can incorporate these specifics in to.
Do: Keep it to yourself - In a business environment the only people who should know your passwords are: Your boss, you and your IT company if required. If it is a joint computer and you have the same log in, then another colleague may require it. Apart from that no one else should be able to know or guess. Change your password - Every so often (three months potentially) you should think about generating a new password. However, before doing this check it is okay and always update the relevant people. Use different passwords - Having one password for all your accounts and logins is a very bad idea! Someone gains your password; they then have access to everything.
Do not: Write it down - An easy way for anyone to access your information. Having a note somewhere with your password on it is a sure way for others to gain full access to your tech. If you must write it down, use a reminder sentence as to what it is, keep it somewhere no one would think to look and never detail what it is for. Blank spaces - Try not to add blank spaces in your password. Instead use connectives. These are easily forgotten and can confuse you when typing it in. Alphabet - Having a series of number or letters shouldn't be considered. E.g. 123456 or ABCDEF.
Known as malware, a virus can be extremely detrimental to the running of your computer. The malware may have different objectives in mind, however most commonly they will destroy files, steal data and damage your computer. But how do you know if you have one?
Have you noticed a difference in the speed of your machine? This includes starting up your PC, navigating through your files, within your internet browser and opening programs. This is one of many tell- tale signs for a virus.
A virus likes to make your computer as slow and as unresponsive as possible. Pushing your machine to its limit is part of the attack. Part of this process is to flood your machine with malicious files and reduce file storage levels. As well as this some malware types like to delete files or encrypt them so you can't access your data.
Are you finding your machine is automatically closing down and restarting? Does your system freeze randomly? Are you seeing strange pop ups and error messages? If so, get your machine checked immediately. Malware can disable the security on your machine. Are you trying to complete a scan or install anti - virus and it isn't working? The virus wants to live on within your PC and so has disabled your ability to diagnose and potentially destroy. It is likely that the malware will try to replicate and expand its reach. This is easily done through sending messages with links to your contacts, either via social media or just through email. If a person sees a link sent from yourself and clicks on it - their machine will also likely become infected. Continuous noise from the hard disk in your machine, even when you aren't using it, is also a sign of a virus. If your internet usage is extremely high, this could mean the virus is sending information back and forth.
It is hard to understand (even when following these tips), if you really have completely destroyed all traces of malware on your machine. Follow these steps and do what you can, but it is always best to have a trained professional completely safety check your machine.
Install a well known, well rated malware scanner - 'Malwarebytes' is a great option. Use it weekly or fortnightly, run a scan in the background whilst completing your usual tasks. Delete any files found, for example PUP's Adware and Malware.
Having a good anti-virus software (security agent) is a good idea. We offer our clients Trend Micro which we rate highly and use ourselves.
Don't download suspicious content from the internet - It is tempting to just download what you require from the internet, and many places are offering this service for free. If it seems too good to be true - it probably is. Links - When opening emails, do not click on links unless you know the person, and even then, be wary. Create dialogue with the person sending and ensure this is correct. If you are unsure and require help. Please give us a call. It is better to be safe than sorry. Malware can cause irreversible damage to your machine and if spread, it can shut down your business.
For those of you who aren’t familiar with Yell. Like the old directories, Yell hosts all company data. You can have a basic free appearance to add visibility to your business. Or you can pay to have a spot within a specified map region. This improves your visibility on Google and to people requiring your services in the area. The great thing about Yell is that you can monitor your progress, change your profile information, add photos and invite your customers to review you. Another feature of Yell is that people can contact you asking for your services. Most of the time it is effective, you contact the person back and start creating a business relationship. However, a percentage of the time you receive spam, or people trying to send you a virus and access your machine. So how does this scam work?
They contact you through message on yell asking for you to email them with their personal email. You email them using the email and then they reply. The reply will usually contain a link they want you to click on ‘to show you what they require’. Clicking links in emails is dangerous, let alone from someone you don’t know. If you click the link it will either lead to a virus download, or for you to log in to some sort of account. Don’t do this! It is a fake page they have created to harvest your information.
How do you know it is a scam?
Here are some pictures showing you what happens. Of course, we didn’t click on the link and so we don’t know the exact scam this person was attempting to pull. But after scanning the link in the email, we realized it was malicious. There are other detailed cases of this happening.
This is a phishing scam. They will use your account information: potentially scamming you via taking funds, holding information hostage, or through downloading a virus of some sort, and controlling your machine.